Undocumented Commands Found In Bluetooth Chip Manufactured in China Used By a Billion Devices.
(www.tarlogic.com)
from Tea@programming.dev to cybersecurity@infosec.pub on 08 Mar 2025 21:06
https://programming.dev/post/26583285
from Tea@programming.dev to cybersecurity@infosec.pub on 08 Mar 2025 21:06
https://programming.dev/post/26583285
Source Link Privacy.
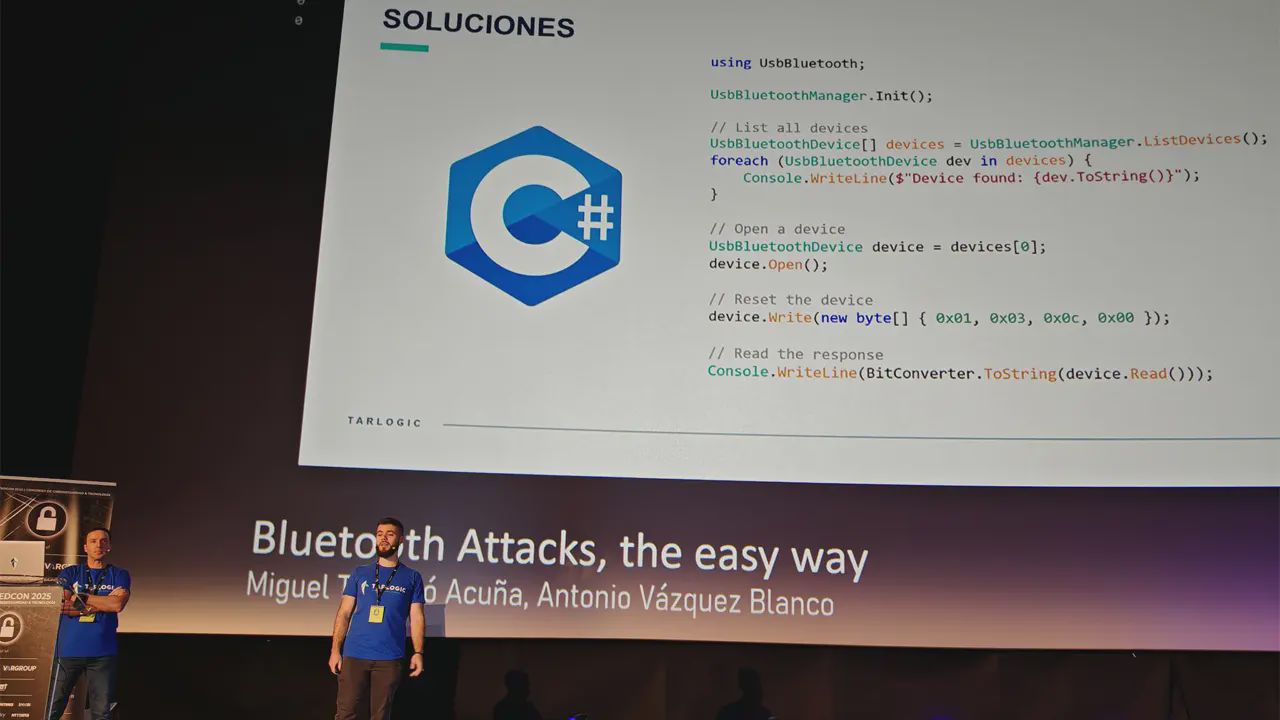
Tarlogic Security has detected a backdoor in the ESP32, a microcontroller that enables WiFi and Bluetooth connection and is present in millions of mass-market IoT devices. Exploitation of this backdoor would allow hostile actors to conduct impersonation attacks and permanently infect sensitive devices such as mobile phones, computers, smart locks or medical equipment by bypassing code audit controls.
Update: The ESP32 “backdoor” that wasn’t.
threaded - newest
<img alt="" src="https://lemmy.world/pictrs/image/287db531-343d-4c10-b30f-93caee11cebc.jpeg">
Yeah. We found the thing we were pretty sure was there!
Though, if it’s really just local debug commands, then the usual “malice vs stupidity” debate is still up for grabs.
That is a big one. IoT lives off ESP32.
Here is hoping this will at least make it easier to take back control of tuya devices
And then there is trump, the illegitimate president, Russian stooge, trying to repeal the CHIPS act.
Well, at least nobody uses that tech. /s
It’s not a backdoor, it’s a jailbreak. Sounds like they left the debug functionality enabled but just undocumented.
Edit: They’re undocumented HCI commands, that’s the protocol the host (aka CPU) uses to talk to the chip, not a remote device.
Since when HCI is backdoor ? Someone doesn’t understand how bluetooth works. HCI allows for vendor extensions by design. bluetooth.com/…/host-controller-interface-functio…
lemmy.world/post/26559432