How NSA Can Spy on Air-Gapped Networks? Meet FIREWALK
(www.youtube.com)
from kugmo@sh.itjust.works to cybersecurity@sh.itjust.works on 02 May 17:25
https://sh.itjust.works/post/37162345
from kugmo@sh.itjust.works to cybersecurity@sh.itjust.works on 02 May 17:25
https://sh.itjust.works/post/37162345
Came out in 2008 and leaked in 2013, the glowies have been able to send out malicious packets from air-gapped networks for exuberant prices.
threaded - newest
Anyone watched the video willing to share how?
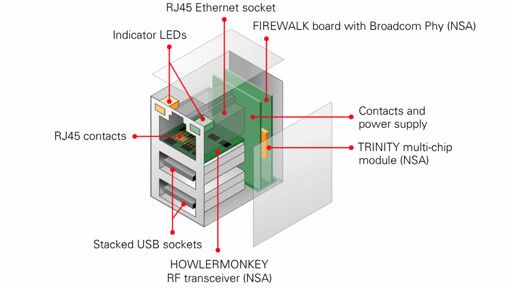
Work for the NSA, seize package of a computer from person you want to spy on, install RJ45 port with hardware backdoor that also has RF emitter, gather the intercepted packets with RF receiver within distance.
www.schneier.com/blog/…/firewalk_nsa_ex.html
Thank you kind stranger.
I also found another website that has some images and bit more details if anyone interested
www.cryptomuseum.com/covert/bugs/…/index.htm
It’s a combination of compromising the hardware gigabit connector on the motherboard, and embedding within that connector a hidden rf device that can exfiltrate data over a wireless signal, effectively jumping across that air gap in place.
It details how the NSA captured hardware shipments in transit and replaced them with the firewalk compromised hardware and then let the shipments proceed to their intended recipient.
It’s an 11 minute video, and a decent watch.
They put an SDR into Ethernet ports. This let them inject exploits and exfil data across air gaps using local agents or proxies who merely got close to the device.
“Came out in 2008 and leaked in 2013”
17 years ago they had this…
Ah, there’s other ways too… see the video with a drone watching HDD LEDs.
Needs malware to do the LED thing of course, oh, and deaf security that aren’t concerned by a drone hovering outside a window every night, but apart from that, it’s foolproof.
“How can NSA–?” is a question.
“How NSA can–” is a statement.