from federino@programming.dev to linux@lemmy.ml on 22 Jun 2024 22:49
https://programming.dev/post/15901372
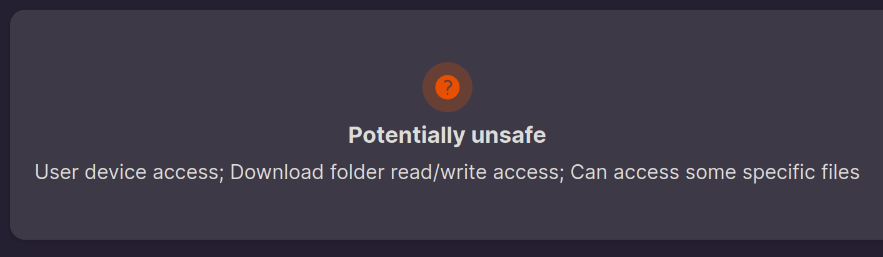
Imagine your friend that does not know anything about linux, don’t you think this would make them not install the firefox flatpak and potentially think that linux is unsafe?
I ask this because I believe we must be careful and make small changes to welcome new users in the future, we have to make them as much comfortable as possible when experimenting with a new O.S
I believe this warning could have a less alarming design, saying something like “This app can use elevated permissions. What does this mean?” with the “What does this mean?” text as a clickable URL that shows the user that this may cause security risks. I mean, is kind of a contradiction to have “verified” on the app and a red warning saying “Potentially unsafe”, the user will think “well, should I trust this or not??”

threaded - newest
Yes, but also… It’s true. Browsers are the number one way folks get viruses.
It’s not specific to browsers, but to every flatpak that is verified and has the potentially unsafe warning.
“Verified” doesn’t mean too much to privacy advocates. There have been incidents. I indeed want to check what my app is going to access before installing it.
I think it’s okay to check what the app is going to access in your system. I’m just talking about the warning design, this comment suggests a different approach for a less alarming design.
Ah, very good point! If we all had the dedication for UX like you do, Linux would be so so so perfect.
Which is hilarious because desktop apps have always had the capability to spy on all other apps and steal all your data.
On bad operating systems like Linux, yes. ;)
You’re thinking of operating systems that give unrestricted access to all parts of a computer that aren’t memory or the camera. That would everything^1^, actually.
^1^ There’s also Linux with properly-configured SELinux, but good luck with that on a distro that isn’t focused on opsec.
So in other words, I’m thinking of Linux
If you’re willing to admit that you’re denigrating an operating system for having the same flaws as the one you prefer and are being a massive hypocrite in doing so, sure.
You’ve lost me on this one. No idea what you mean. But either way, I think you should take my comment just a bit less seriously.
Fedora has pretty good SELinux configured out of the box, and isn’t focused on opsec. It’s just sane defaults and proper limitations to access. It also switched to Walyand-by-default this release, completely removing X11 from the default packages, which mitigates many of the “app spying on other app” scenarios that a previous user in the thread was talking about. That’s not to say that Fedora is the pinnacle of Linux security or anything, but it comes with pretty good defaults for the average user. You’d have to get into kernel hardening and deep into SELinux to do better as an end user, which is not something that most users are inclined to spend time or energy on.
.
That’s funny because we have been shipping a commercial Windows app since XP that is keylogger-based using SetWindowsHookEx, and it has only tripped users’ antivirus maybe 1 or 2 times in 20 years.
EasyOS is the first distro I’ve seen that at least runs every app as its own user by default, similar to Android.
Yes but surely you’re aware that even the most new-user-friendly distros and their tools aren’t necessarily aimed at new users.
That warning is a perfect example of how Linux developers choose which hill to die on. They post a warning for an app that everyone knows can deliver bad times to two camps of users; those that know and don’t care and those that don’t understand the warning. If we could quantify the helpfulness of that warning, odds are that it saved 0 users from malicious action from that avenue of attack.
Never expect Linux as a whole to be “helpful” to the new crowd.
.
Which is why I said “linux as a whole”. Many distros will try to undo the nerdery and neckbeardism that is built into the parent distros but as a whole, linux is going to always be less welcoming to a new user than someone that’s used to useless warnings and repeated password entries for elevated privileges. Being safer and being new-user-friendly rarely go hand in hand.
Not all user friendly distros have a parent distro. Checkout Solus.
There are sometimes things upstream causing problems. The Linux kernel itself isn’t one of them though as Linus is pretty adamant that Linux distributions should be easy to setup and use. KDE is also designed to be pretty friendly while being customizable still. The main issues seem to come from apps and distributions.
I like flatpaks and flathub, but this is just something they do badly. I think as well they also have “probably safe” which is just as unhelpful… And what does “access certain files and folders” even mean!?
I think they should just follow the example of every other app store; list the permissions in an easily understandable list and let the user decide whether or not they are comfortable with it.
Totally agree. The “verified” label will give new users enough comfort, and the ones who wish to know more will read the permissions.
When I look at Firefox in Discover, it only shows the list of permissions the flatpak will be given out of the box, with no warning of it being “potentially unsafe.” This certainly does seem like the better way to handle it.
Also, the warning on the Flathub website is clickable - it expands into the full permissions list. Why it defaults to “no information except maybe dangerous” is beyond me.
That is a clickable menu that explains exactly what the permissions are.
isn’t flatpak by definition relying on a second software source, hence 2x as much risk as relying on a single source (your OS repo)?
How much sandboxing is your distro generally doing?
beyond root processes, none that I am aware of. Hence I configured all my internet applications and steam to run in a jail :) firejail & bubblewrap come as native packages, unlike the flatpak contents
A distro has thousands of independent sources. No your distro doesn’t audit them all, barely any.
“barely any” is neither entirely accurate, nor does it excuse the use of flatpaks.
.
I just typed “xdg-download:𝗰𝗿𝗲𝗮𝘁𝗲” into flatseal, my browser is safe af now.
In short, no
.
Huh? Flatpaks are great and there’s no real reason why they’d be unsuitable for a new user.
Many flatpaks are not aware of their sandbox and thus have a bad ux.
E.g. flatpak Steam can’t access SteamLibraries at a non-default location, unless the user manually allows the path through flatseal. The same is true for other similar apps which don’t use the file portal.
Issues like this are unexpected for new users and thus it can be argued that flatpak aren’t a good recommendation for new users. I personally disagree because most flatpak work flawlessly and work everywhere independent of a users distro.
.
Yesss! It’s too aggressive
those warnings on mint and flathub are so ridiculous, there’s no difference between those and official ones, somebody could just as easily put something nefarious in any flatpak
Firefox on flathub is an official one, that’s not what this warning is.
In my opinion, those warnings are not used to help users but to shame developpers for not trully sandboxing and verifying their apps. Developpers know that having this warning will decrease the number of users downloading it. The goal in the long run is to improve app sandboxing and security.
By not letting the user import/export addon settings, bookmarks?
Btw, i hate the opinion that the dev must babysit his users. It makes software worse, not better, look at Firefox’s profille folder for an example. If you have to, make an intro to train them.
I’m not 100% confident but I thought you could use portals to access individual files outside of the sandbox
You could but where is fails is when you open one html file that then needs to loads the other files that are needed by the first.
You can not allow chain loading like this, it would bypass the sandbox.
One way of working around this would to allow the option of passing a whole folder and sub folders to the program.
The other and much harder option would be a per program portal filter that can read the html file. then workout what files that html file needs and offer that list of files to the user.
The lazy work around is allow read access to $HOME and deny access to some files and folders like .ssh
Makes sense, but at least this would generally be out of a normal users usage case (multi-file documents), and so the power user could probably just open flatseal.
For things like bookmarks it’d work fine, and by extension make the sandbox more secure
I would not be so sure. Firefox has a “save web page as…” option which saves the html page and all other files needed into a sub folder.
Without better handling of reading and writing files the sandbox will break that builtin function. another way of working around this. would be to change firefox to save the web page into one file. Maybe something a .html+zip file that firefox would know how to open. However that would lock other browsers out without manualy unziping it first.
Getting sandboxing right with powerful programs is very hard and I feel the tooling is still not here yet.
You can choose folders in the portal now.
My bad, i thought that was included in file system access.
Completely agree. Training normies to click OK on warnings like this is a no-good terrible idea.
They shouldn’t click on on this tho
Training users to click on this shit is the same reason people wipe their desktop by ignoring “Yes I know what I am doing” warnings.
someone is not a fan of LTT
Good.
People need to view out of channel software with a hairy eyeball.
Hell, I run Debian all over and it’s absurd that the main repositories don’t do checksums on downloaded packages!
WAIT THEY DON’T ???
yeah apt just trusts the server if it properly identifies itself
the barrier to entry for attacking that seems pretty high though
if that freaks you out, switch to a rhel derivative, they got a shiny progress bar
Interesting, but switching will be difficult, unfortunately…
Thanks for the info
I think it’s absurd that most distros have no tools whatsoever for doing regular checksums of their own files. Windows certainly got that part right IMO.
I’m double checking this myself now, but there are plenty of tools (debsum) they’re just not part of the default implementation as of last time I looked.
Right, I’m talking about like periodic or real-time scanning and alerting, which DISM/SFC on windows does.
i’m almost 100% that debsums on apt stuff and the --verify flag in rpm distros do what sfc did. (kinda, debsums and --verify check against a list of checksums from the repo, i’m pretty sure sfc cracks open an actual known version of the files and compares em with whats on disk)
idk what dism does.
They should be worried. We don’t want them comfortable.
So many negative things have entered our culture bc people don’t care about dangers. Nearly every app should have a warning
They should not be worried, they should be educated.
If you worry a new user enough they’ll go back to Windows or Apple because there’s less scary warnings there.
We need to make the transition as pain free as possible. Learning about the joys of kernel compilation and SELinux can come later.
The first step is "Hey, this is as usable as Windows, without stupid ads in the start menu.
No. If you put a warning on every app (except for the most trivial ones that don’t actually do anything useful) then the warnings mean nothing. The become something more than ass-covering legal(ish) BS.
Apps could start improving to remove the warnings…
What do you mean by “improving”? This alarming warning appears because Firefox requires permissions. Let us look at the permissions listed there:
App permissions should not be about “this app cannot be trusted because it asks for scary scary permissions”. They should be about “take a look at the list of permissions the app requests and determine whether or not it make sense for such an app to need such permissions”.
To 1.:
driinstead ofallwould handle hardware-accelerated rendering. Then some webcams or controllers won’t be accessible though. This one’s a bit complicated, since the necessary portals for e.g. generic USB device access aren’t yet there.To 2.: portals should be used instead of that. Using them doesn’t require these permissions.
To 3.: click on details and see. This is Flathub making it easy to understand for users.
Permissions should make clear whatever dangerous things an app can do. If not, why do all this effort of isolation? Firefox could delete everything in downloads, either by accident on Mozilla’s side, or a privilege escalation. If the app used portals instead, it couldn’t, at least without user interaction. Or a browser security vulnerability could open up any USB devices to webpages. It’s all about what could happen with granted permissions. And these can 100 % be fixed in at least some way.
So it would be how in the US half of all products have a warning saying they cause cancer thanks to California proposition 65? No thanks.
If “nearly every app” that people already use suddenly has a big warning on it, people will quickly decide the warnings are meaningless and start ignoring them, like Prop 65 warnings. Congratulations, we’ve moved the needle backwards.
You have to meet people where they’re at. I finally switched to Linux when MS introduced a feature I wanted no part in (Recall AI), but I would have given up within a day or two if the transition hadn’t been basically seamless. I was able to pick up right where I left off, using all the same apps I did on Windows
except MusicBee RIP, but now I’m in a better position than before, on an open-source OS instead of closed-source. Now there’s a little less friction between me and better, freer software.prop 65 warnings are indeed useless
To be fair, the fact that browsers are allowed to do so much that this warning has to be shown is more an indictment on the current state of browsers (which at this point are almost like installing VMWare and a virtual machine on your computer!) than on something something Firefox or something something Flatpak.
I mean yes, how exactly would you want the web to work? In order for it to be secure we need website code to run in an isolated environment. Modern web browsers have gotten pretty good at this.
Though we say it’s a JavaScript Virtual Machine it’s not the kind of virtual machine you are thinking of. It just means it’s being interpreted in a certain environment rather than compiles code running natively. It’s not like a whole OS. Running a web browser in a Virtual Machine is unironically a method to improve security; checkout Qubes OS for an example.
Also the permissions it’s asking for aren’t that serious. Basically GPU access and download folder access.
Text and images and hyperlinks; maybe audio and video if you’re lucky and you can prove you can be trusted. No such thing as scripting, or if it’s allowed, only in a limited manner with no such thing as “eval” and obfuscation and no ability to add or delete nodes from the DOM (or if it’s allowed, those nodes must reflect under View Source / CTRL+U). No such things as loading a javascript audioplayer that tries to mix 123456 weird sources, just link me the .m3u direct to the audio stream’s .mp3 file, or even better an .opus.
Definitively no DRM.
If any such thing as GPU access is provided it should be to deposit data, not to run code.
Those things still require a GPU to render efficiently.
All the other stuff you talk about don’t need a GPU or really any systems permissions at all. So even if the web changes to your twisted view the flatpak would still require the same permissions. All you’ve just proven is that you don’t understand technology.
You don’t know what a GPU is apparently. Regardless the same access is needed for both.
Also you use Lemmy, which requires scripting. Pretty much every online game, shopping website, calculator, and so on require scripting of some kind. Scripting isn’t just for bad things like tracking. It makes a lot of cool stuff possible, that you doubtlessly use everyday. As a plus it’s generally more secure to use a web app than have a myriad of different programs or applets replace all these different things, as websites are sandboxed. There is a reason JavaScript replaced Flash and Java applets.
You’re confusing a technology problem with a society/capitalism problem.
What does ‘user device access’ mean?
Clicking the potentially unsafe item lists the exact permissions.
It can access hardware devices, like your webcam or game controller. Likely --device=all in flatpak speak but I haven’t looked.
Maybe access to connected devices (e.g. your computer components or the phone you have plugged in to your computer)
I’m a firm believer that regardless of operating system that a warning message saying that installing something could cause harm to your device definitely makes people think twice about installation if they’re not tech savvy (AKA know more than the bare minimum anymore). It’s definitely intentional that the large companies responsible scare you away from doing the things you want because they want you locked into doing things the way they want.
Just reminding folks that just because it’s flatpak’d, doesn’t mean it’s sandboxed. But they probably should add some general click here for more info.
This should have been much more well thought out The wording, image, buttons, specific wording for each page.
They really screwed the pooch.
Another 4-6 months minimum before release. But quarterly numbers must be met.
pretty standard compared to OSs like Android and iOS. i think the mobile OSs, at least recently, have done better at this; they don’t ask for permission until they need it. want to import bookmarks? i need file system access for that. want to open your webcam? i need device access. doing it all upfront leads to all the problems mentioned in this thread: unclear as to why, easy to forget what access you’ve given, no ability to deny a subset of options, etc.
does Linux have APIs for that? I know macOS does, not sure about either windows or Linux allowing capability security like that
not likely. i think it requires a lot of systems working together
If you use Debian-based linux (Ubuntu, Minut, others), Mozilla recommends getting the package directly from their respository rather than flatpak or other repos.
Personally, I saw a major performance increase on my low-powered laptop when I switched from flatpak to the Mozilla package.
blog.mozilla.org/…/4-reasons-to-try-mozillas-new-…
That’s nice, I think I’ll switch from Firefox ESR on Debian!
I’ve tried both on my low powered HTPC and came to the same conclusion - especially noticeable where video acceleration is concerned
In defense of this warning, when I first put my application on Flathub, I had it because of how file i/o worked (didn’t support XDG portals, so needed home folder access to save properly). It did actually motivate me to get things working with portals to not request the extra permissions and get the green “safe” marker.
A lot of apps will always be “unsafe” because they do things that requires hardware access, though, so I could see them wanting something more nuanced.
To be fair, if a naive user is going to get a virus, there’s a very high chance a browser will be involved.
Users should be afraid of the malware that is default firefox. Why do you think so many people use forks?
as opposed to chrome?
Chrome being worse than Firefox doesn’t make Firefox’s default telemetry, adware, and DoH to cloudflare good. When the bar is Chrome, essentially any browser passes.
Would you mind explaining?
Telemetry you can’t easily disable (requires modifying about:config, can change on update), Glean (nastier than anything in chrome), DoH to cloudflare, pocket (adware), Anonym.
www.jwz.org/blog/2024/06/mozillas-original-sin/ mozilla “saving the web”. If you want to save the web, use something like qutebrowser, luakit, or falkon with drm compiled out.
jwz.org/…/mozilla-is-an-advertising-company-now/