FUSE Passthrough Mode Merged For Linux 6.9
(www.phoronix.com)
from ylai@lemmy.ml to linux@lemmy.ml on 15 Mar 2024 20:16
https://lemmy.ml/post/13211910
from ylai@lemmy.ml to linux@lemmy.ml on 15 Mar 2024 20:16
https://lemmy.ml/post/13211910
threaded - newest
This is the best summary I could come up with:
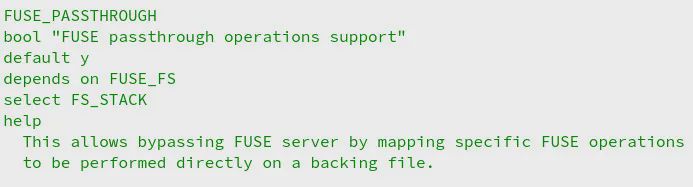
The FUSE passthrough mode that’s been years in the making for better performance was merged upstream today for the in-development Linux 6.9 kernel!
Last month I wrote that FUSE passthrough might land for Linux 6.9 after noticing the patches finally appear in FUSE.git’s “for-next” branch.
This feature was indeed sent in as part of the FUSE updates for Linux 6.9 and today Linus Torvalds merged it upstream.
The FUSE merge for Linux 6.9 sums up the feature as: Add passthrough mode for regular file I/O.
This allows performing read and write (also via memory maps) on a backing file without incurring the overhead of roundtrips to userspace.
For now this is only allowed to privileged servers, but this limitation will go away in the future FUSE for Linux 6.9 also fixes up an interaction issue in direct I/O mode with memory maps, exposes file-system tags through sysfs for VirtIOFS, and various other fixes.
The original article contains 248 words, the summary contains 153 words. Saved 38%. I’m a bot and I’m open source!
The website doesn’t open with cookies disabled. That’s kinda sus. Also the kernel version number is sus. I suppose the OP is an imp
Not sure what called for this blatant personal attack. My post history speaks for itself, quite in comparison to yours. And Phoronix is well-known Linux website, and its test suite is in fact even referenced in various regression tests/patches in LKML (also not sure what/if any kind of kernel development you have done).
Mister, I was joking. The website is indeed sus (and the popularity is not a good defense for it) but it doesn’t mean you are. It’s just an interesting coincidence of a sus website and a sus number. That’s it
Well, if you have a constructive suggestion which site to link instead regarding kernel developments, I am all ears:
Well since kernel development is one of the harder topics in the whole IT industry, it’s understandable that the websites that make news about it do need to use privacy invasive ways to earn money (whether it’s a paywall or an extremely invasive data collection) because the audience is stable and extremely small. But it does not make them safe in any way. They’re still sus in terms of privacy (which is what I meant). I’m far far away from anything like kernel development so I can’t suggest anything related to it unfortunately. I think it will be the best choice to admit that my sense of humour, as well as my communication abilities, is far from being decent enough not to create misunderstandings, suspicions and double meanings like in this case, and end this discussion. Almost all the arguments on the internet only spread hate and aggression anyways and I don’t want that (you were not aggressive though)
As a fellow poor communicator, I just want to say that I appreciate your self-awareness.
Thank you, mister. Though after looking at your post history I can say that your communication ability is 1000% better than mine
ඞ
Does that mean that all Fuse filesystems automatically gets this huge boost ?
In the beginning, only privileged ones will be allowed to run in pass-through mode. But goal/roadmap calls for all FUSE filesystems eventually to have this near-native performance.
I feel I should know this in my bones after so many years, but does ‘privileged’ in kernel context also include ‘sudo/sudo su’ elevated users ? I wonder if the kernel distinguish between pure root, and elevated user …or if it even matters here ?
Anyway, this is cool. There’s a ton of crazy file systems that just didn’t pan out bc of speed issues. I’ll just leave these links to filesystems.
github.com/libfuse/libfuse/wiki/Filesystems A ton of cool ideas!.. I need my AI to have access via fuse. en.wikipedia.org/wiki/Filesystem_in_Userspace?lan… less crazy systems but probably stable projects
Thanks for sharing the info!
sudo allows so run actions as root, so I would say yes.
But a privileged filesystem might not be invoked by the user, it may be a process running as root.
How would the update affect stuff like a GoCryptFS volume which I mount and use periodically but not all the time? Would those files be processed much faster than previously?
Note: Android kernel has had this since 12 because FUSE is used to enforce permissions and to emulate legacy storage types.
source.android.com/docs/core/…/fuse-passthrough
From the patch back in 2016: