Auto DNS poisoning: while charging Android smartphone via computer it is possible to perform automated and even remotely controlled DNS poisoning without any user interaction
(www.mobile-hacker.com)
from repostbot33@lemmy.world to netsec@lemmy.world on 20 Feb 2024 12:00
https://lemmy.world/post/12186236
from repostbot33@lemmy.world to netsec@lemmy.world on 20 Feb 2024 12:00
https://lemmy.world/post/12186236
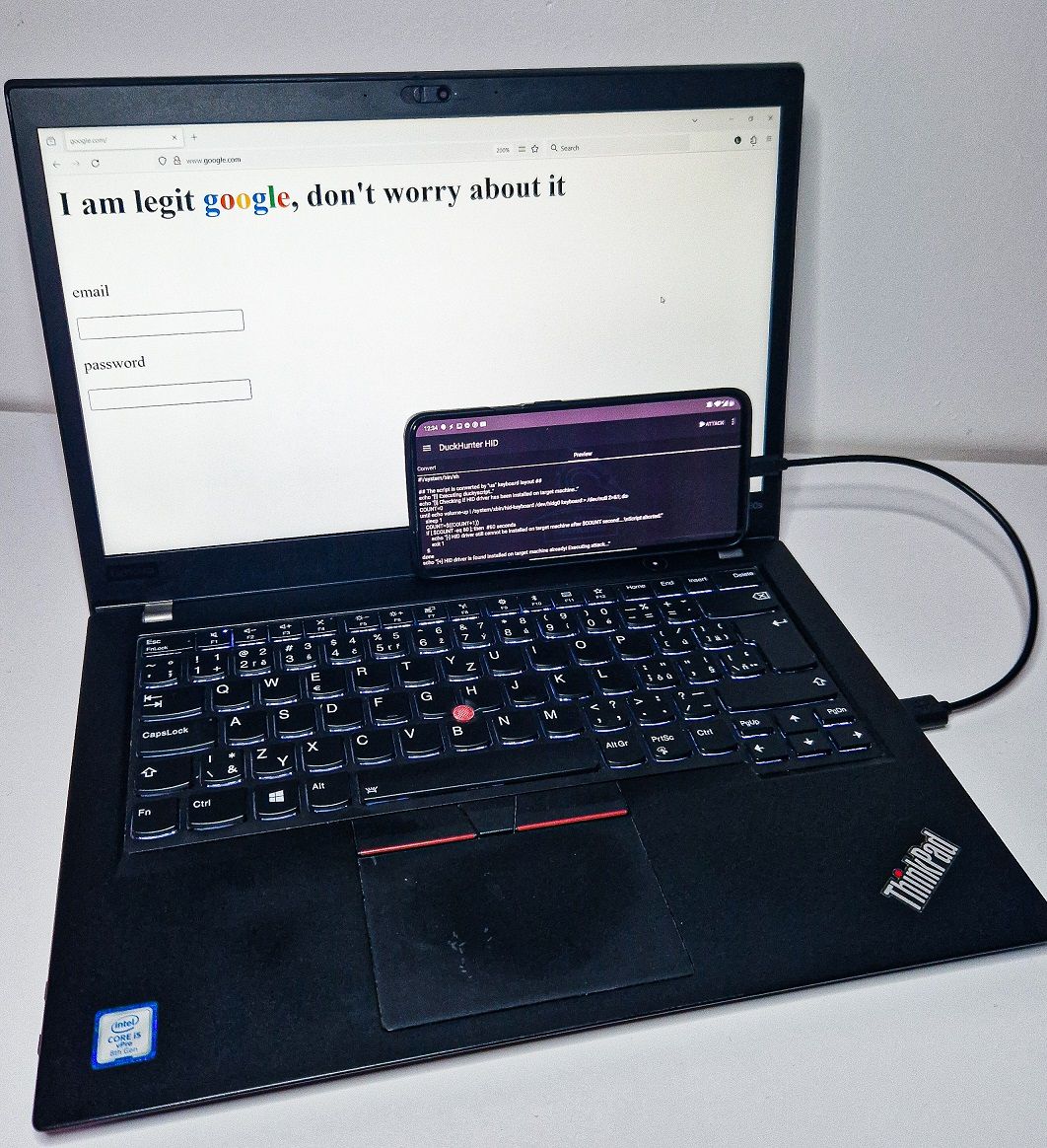
threaded - newest
So, to achieve this:
Sounds like darwinism.
Yeah. It was pretty interesting to hear the details of pretending to be a HID device and how you could use it in practice to make malicious changes to the host computer. But surely adding to /etc/hosts is not the most preferred sneaky thing you can do with your unrestricted access.
Isnt the average Windows user not logged in as admin?
Most Americans I know own their own computer. Unless it’s with young kids in the house, every individual windows PC is one account with admin access.
I also own my computer. Doesn’t hold me back to remove my user all admin rights. If you still log in with admin rights, being hacked by a charging phone won’t be the first bad thing happening to your system.
You would also get several prompts asking if you want to do this, both from Windows under UAC (by default, even if you can escalate), the Android driver, and the phone itself. It’s rarely the case now that Windows users execute privileged actions without notification, but it’s possible.
I don’t want to discourage people testing ways to compromise security for the good of everyone, but this is a well known vector and a lot of jumps have to succeed to give the attacker value.
You can cut down a lot of room for failure by just using a rubber ducky USB instead. It doesnt have to be an Android phone. Even then, there’s more than a few controls in the way.
No one pays attention to the prompts. If you’ve ever watched a standard computer user they click away a prompt as fast as it appears without even reading it.
So I understand better, could you explain the scenario where you would use this and what it would get you as the attacker?
Is it like: “Hey bud, please plug my phone into your computer.” Then, they click through everything, you get privileged execution, and you choose to modify the hosts file?
You believe that would have a high chance of success? What do you get afterwards?
Would be more robust for the phone to say “hey, I’m your new network interface” (a.k.a. usb tethering). AFAIK, it’d use DNS provided by the device.
The pro’s are that it works on all the os’es ootb and doesn’t create suspicious windows on connection, so you don’t need to distract the victim