[Discussion] Auto-disable Remote Access on Vunerable Selfhosted Services
from Deemo@bookwormstory.social to selfhosted@lemmy.world on 25 May 2024 23:16
https://bookwormstory.social/post/1846284
from Deemo@bookwormstory.social to selfhosted@lemmy.world on 25 May 2024 23:16
https://bookwormstory.social/post/1846284
Hi guys I was wondering if there is a streamlined way to disable remote acess to a selfhosted service (say at a reverse proxy level) if a published security vunerability is present.
I know, ideally you want to keep all your selfhosted services up to date. However on certain selfhosted service auto updates may not be viable (due to major changes between updates) and you being unavailable 24/7 to respond to vunerabilities.
Curious on your thoughts and suggestions. So far the only middle ground I can find is realying on a vpn wireguard, tailscale, etc.
Page regarding homeassistant remote ui autodisable: www.nabucasa.com/config/remote/
threaded - newest
If you know of a data source for these vulnerabilities, I’m all ears. Because currently, that aggregation work is done by companies selling the feeds for quite a lot of money.
Personally, I’d just put everything behind a VPN. The attack surface is much smaller.
Are you refering locations for vulnerability disclosure or are you more referring to bug bounty?
Fair enough
I’m not the commenter but I can take a guess - I would assume “data source” refers to a machine readable database or aggregator.
Making the system capable of turning off a generic external service in an automated way isn’t necessarily trivial, but it’s doable given appropriate systems.
Knowing when to turn a service off is going to be the million dollar question. It not only has to determine what the backend application version is during its periodic health check, it also needs to then make an autonomous decision that a vulnerability exists and is severe enough to take action.
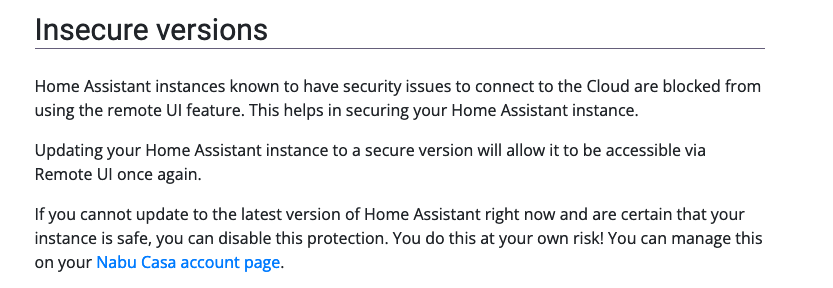
Home Assistant probably provides a “safe list” of versions that instances regularly pull down and automatically disconnect if they determine themselves to be affected, or, of the remote UI connection passes through the Home Assistant Central servers, the Central servers could maintain that safety database and off switch. (Note - I don’t have a home assistant so I can’t check myself)
I think this is how home assistant handles it. When they put out a cve they can update the insecure version list which makes nabucasa refuse remote forwarding (until you update).
Initially I was just thinking if a open-source project is on github and uses the security disclosure feature if it would be possible to pull data from it and disable remote acess (either by auto shutting down the service or simply disabling routing on a reverse proxy).
Having a system that does without a security disclosure list from a project maintainer would be far mor difficult like having the proxy disable one of your services if it detects a vulnerability in a dependency.
I tried this for 2 months with tailscale and love it, however having it run 24/7 on both my wife’s and my phone was too much. It literally wiped out the battery on my wife’s iPhone 12 unless she charged it in the middle of the day. I lost about 40% more battery throughout the day on my android. I had to switch back to cloudflare and nginx proxy manager for now.
Hmm. It shouldn’t do that. If you try it again, I’d check the configuration, and if you verify it with the Android battery metrics, open an issue.
I assume it also supports split tunneling, which might help.
Thats a really neat idea but I’m not sure its practical. Definitely putting everything you can behind a VPN is the best bet. Only things I dont have behind VPN/local only are things my extended family use and are on a different vlan.
Doesn’t the NIST in the US publish a database of vulnerabilities? nvd.nist.gov/developers/vulnerabilities
If you figure it out, I know several companies that would be more than willing to drop 7 figures a year to license the tech from you
I’m available for part-time 😁
I can’t help here, but:
The title would be less confusing if you didn’t cram everything in one sentence. Potential help might be driven off by this, i was almost too.
Sorry about that (didn’t think that far when making the post 🫠 ).
I updated the title
The first thing that comes to mind is a combination between SBOMs generated for your self-hosted services (trivy, syfy, etc) which are pushed to OWASP Dependency-Track and whenever some vulnebrabilies are detected (note: you’ll get lot of notifications if the application is using a lot of libraries), trigger an event (not sure if node red can help here) which would run a script to disabled the vhost. (just a thought. I haven’t seen an actual solution)
Acronyms, initialisms, abbreviations, contractions, and other phrases which expand to something larger, that I’ve seen in this thread:
[Thread #762 for this sub, first seen 27th May 2024, 00:15] [FAQ] [Full list] [Contact] [Source code]